一定要知道的 OWASP top 10:2017 Web 開發攻防之道
2020-10-08
摘要 OWASP top 10:2017 各項常見風險的介紹與對應的攻擊、防禦之道 ⚔️🛡️
Top 10 Web Application Security Risks
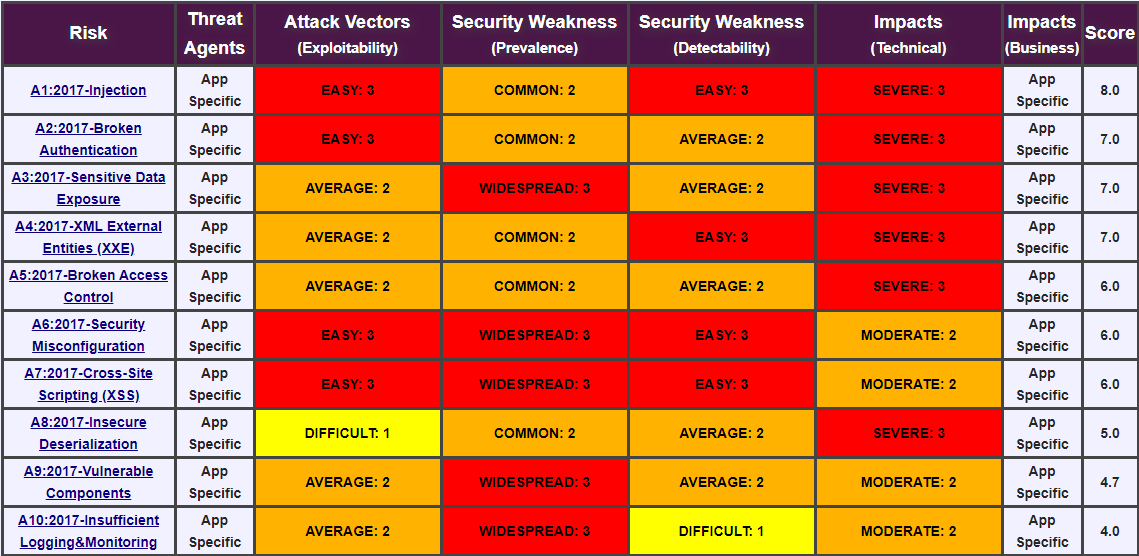
Injection
Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker's hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
惡意的資料被傳入應用程式(Url, Query String, Headers, Input field, etc),被應用程式詮釋為 SQL, Command 以及 Code 的一部分,行出預期外的結果,可能造成資料與系統的損失。
⚔️ 攻擊之道:
- 對任何輸入欄位手工填空
- sqlmap
🛡️ 防禦之道:
- 參數化查詢 (Parameter Query)
- 輸入內容檢查 (Input Sanitization)
- Filter Request 篩選規則輔助
Broken Authentication
Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users' identities temporarily or permanently.
驗證機制不正確實做,另惡意使用者有偽造 (Spoofing) 身分的機會。
🛡️ 防禦之道:
- Session 逾期時限
- 登出後銷毀 Session 實作
- 不提供重複的 SessionId
- Cookie 設定 HttpOnly 保護 SessionId
- 配合 HTTPS 將 Cookie 設定 SSLRequire 保護 SessionId
Sensitive Data Exposure
Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
敏感的資料未做處理,當其他惡意攻擊成功時,資料被取用時因為無加密處理會以明文的形式流出。
🛡️ 防禦之道:
- 敏感資料存入資料庫時進行雜湊 (hash) 或加密 (encrypt)
- 敏感資料進行遮蔽
XML External Entities (XXE)
Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks.
🛡️ 防禦之道:
- 關閉 DTD
Broken Access Control
Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data, such as access other users' accounts, view sensitive files, modify other users' data, change access rights, etc.
🛡️ 防禦之道:
- 前後端並行的檢查機制
- 特別容易遺忘的權限檢查點:分頁、搜尋
- 輸入內容檢查 (Input Sanitization)
- 避免 Path Traversal
Security Misconfiguration
Security misconfiguration is the most commonly seen issue. This is commonly a result of insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. Not only must all operating systems, frameworks, libraries, and applications be securely configured, but they must be patched/upgraded in a timely fashion.
未停用預設不安全的設定,包括允許預設帳號、密碼,或啟用了不安全、不正確的設定,例如暴露資訊的錯誤訊息等。
🛡️ 防禦之道:
- web.config 的安全設定
- IIS Configuration (Filter Request)
- 停止詳細錯誤訊息
- 停止目錄瀏覽
- 停止預設帳號密碼
- 移除不需要的模組、範例頁面
- 移除測試模式
Cross-Site Scripting XSS
XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript. XSS allows attackers to execute scripts in the victim's browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
藉由 Reflected 或 Stored 的方式將對使用者的瀏覽端執行惡意的 JS Scripts ,可以竊取使用者 cookies 中的敏感資訊如 sessionID 或者將使用者導向惡意的網站。
🛡️ 防禦之道:
- 輸入內容檢查 (Input Sanitization)
- UrlEncode
- HtmlEncode
- JavaScriptEncode
- 設定 HttpOnly
Insecure Deserialization
Insecure deserialization often leads to remote code execution. Even if deserialization flaws do not result in remote code execution, they can be used to perform attacks, including replay attacks, injection attacks, and privilege escalation attacks.
🛡️ 防禦之道:
- 輸入內容檢查 (Input Sanitization)
Using Components with Known Vulnerabilities
Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts.
使用具有漏洞的軟體以及元件,未能及時更新修補漏洞或者在尚未有更新之前停止使用該元件,造成惡意使用者得以 exploit vulnerabilites。
🛡️ 防禦之道:
- 檢查產品、元件於 CVE 的弱點通報
- 保持軟體的更新
- 使用 Open Source Analysis (ex 💲Whitesource)
Insufficient Logging & Monitoring
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Most breach studies show time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
系統紀錄與監測的機制不足,讓 APT 攻擊成為可能,同時在問題發生時沒有辦法尋找惡意行為的軌跡。
🛡️ 防禦之道:
- IIS Logs
- Elmah
- Nlog
- Failed Requests Tracing
- Windows Event Logs
- Performance Logs
- Process Explorer
- Process Monitor
- Fiddle
參考資料
GitHub - OWASP www-project-top-ten
GitHub - OWASP TOP 10
NCCST - OWASP_TOP10_2017
後續行動
閱讀「107 安全資訊系統開發訓練研討會」教材:OWASP_TOP10_2017,完備 OWASP TOP 10:2017 攻防之道。